STANAG
4285 is specified by the NATO (North Atlantic Treaty Organization)
Military Agency for Standardization in "Characteristics of 1200 / 2400 /
3600 Bits per Second Single Tone Modulators / Demodulators for HF Radio
Links" (16. February 1989).
Carrier frequency: 1800 Hz
Manipulation (n-ary): 8-ary PSK (+ BPSK modulated preamble)
Manipulation speed: 2400
Autocorrelation frequency (ACF): 106.7
Carrier frequency: 1800 Hz
Manipulation (n-ary): 8-ary PSK (+ BPSK modulated preamble)
Manipulation speed: 2400
Autocorrelation frequency (ACF): 106.7
Using
different n-ary PSK modulations and FEC (Forward Error Correction)
coding rates, serial binary user information (raw data, or payload)
accepted at the line side input can be transmitted at different user
data rates (measured in bps).
Most STANAG 4285 transmissions are originated from BRASS encrypted
circuits that use encryption devices called "KG-84 Loop". These
circuits send pseudo-encrypted data 24h/7 NOTWITHSTANDING from the
signal that is applied to their input.
This here is 10568.2 IDN NCSA Naples running in sub-mode 600L on USB. As shown by decoder Sorcerer, it's clearly a random encrypted transmission
Let's
have a look at the decoder phase-plane, since they use (at present) the
submode 600L we expect to see a 2-PSK constellation:
The phase-plane might lead us to think that the signal is a 2-PSK... but it is not so: those are the raw-data transported by the signal (payload) and NOT the signal itself !
Well, go on analyzing that same SATANAG-4285 signal using the tool SA-Signals Analizer, from the great Serghei (RIP).
The signal has been isolated from noise and re-sampled at 8000 Hz
thought approximatively, we get a Baud Rate of 2400 and not 600 as declared by the our decoder (but remember that the decoder measures the data rate!).
Measuring the STANG-4285 ACF (Auto Correlation Frequency) we get a value of about 106.7 milliseconds, as expected (106.67); evidently the received signal or the recording are not so clear:
Below the results after running the SA phase-plane tool:
as
expected, the constellation shows an 8-PSK signal (8-ary) running at
2400 baud, along with a 2-PSK payload, as shown by the decoder!
While SA do analyze, the decoder is just doing its job: it doesn't care about envelopes but just the messages inside: this is an important concept that you must have clear when you want to analyze a signal. Let's look at the STANAG-4285 ACF one more time.
Measuring this parameter with SA analyzer we got 106.7
milliseconds, but what using a decoder? No problem, measuring the ACF
using Code300-32 by Hoka we get the value of 32 bit for a STANAG-4285
signal:
while, as seen above, SA shows an ACF of 106.7 msec for the same signal.
Why this difference? and what is the REAL value of the ACF, 32-bit or 106.67 msec ?
This happens just because the simple ACF function used in some decoders doesn't display the ACF of the decoded bitstream, but rather the repetitive pattern of the raw signal itself. Let's have a look at the signal structure.
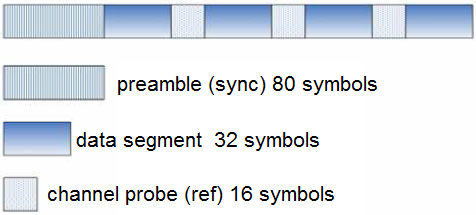
In STANAG-4285 an 80 symbol BPSK preamble is being inserted into the signal every frame (256 symbols) and that's what creates your pattern
In STANAG-4285 an 80 symbol BPSK preamble is being inserted into the signal every frame (256 symbols) and that's what creates your pattern
1000ms/2400Bd = 0.4166667 ms per symbol for a 2400Bd system like S4285
256 symbols x 0.4166667 = 106.67 ms (so you have a repetition every 106.67 ms)
The
primitive "ACF" module of the decoder probably runs the raw signal (not
the bitstream) against a 300 Bd display, which creates a pseudo ACF of
32 bits on a STANAG 4285 signal:
1000ms/300Bd = 3.33333 ms per symbol
32 bits x 3.33333ms = 106.67ms -> and there you have the 32 bit pseudo ACF created by the BPSK inserts every 256 symbols used in STANAG 4285.
32 bits x 3.33333ms = 106.67ms -> and there you have the 32 bit pseudo ACF created by the BPSK inserts every 256 symbols used in STANAG 4285.
Which just goes to show!
Below, an phase-plane example of a STANAG-4285 mode sending null traffic (all zeroes), it could be supposed as an idle mode (no chars was printed in the output screen of the decoder):
The
majority of STANAG-4285 transmissions are encrypted BRASS circuits
using loop encryption devices. These "cipher" devices in use today are
mainly the BID1650 while the new NATO countries use R&S ELCRODAT.
They will send pseudo random encrypted crypto traffic 24h a day - regardless of any input, the station will always send encrypted data as output. This output is in most cases synchronous, only in rare cases will you see asynchronous traffic on these BRASS circuits.Please remember that most stations use 600bps/Long, while there is a number of French and British nodes that use the submode 1200bps/Long. You can find out the right speed and interleaver setting by looking at the error rate of the decoder. When you have selected the correct parameters, you will see an error rate close to 0%.
In order to find out the correct terminal setting, you will need to look at the bitstream output - asynchronous traffic will clearly display the start and stop bits.
They will send pseudo random encrypted crypto traffic 24h a day - regardless of any input, the station will always send encrypted data as output. This output is in most cases synchronous, only in rare cases will you see asynchronous traffic on these BRASS circuits.Please remember that most stations use 600bps/Long, while there is a number of French and British nodes that use the submode 1200bps/Long. You can find out the right speed and interleaver setting by looking at the error rate of the decoder. When you have selected the correct parameters, you will see an error rate close to 0%.
In order to find out the correct terminal setting, you will need to look at the bitstream output - asynchronous traffic will clearly display the start and stop bits.











No comments:
Post a Comment